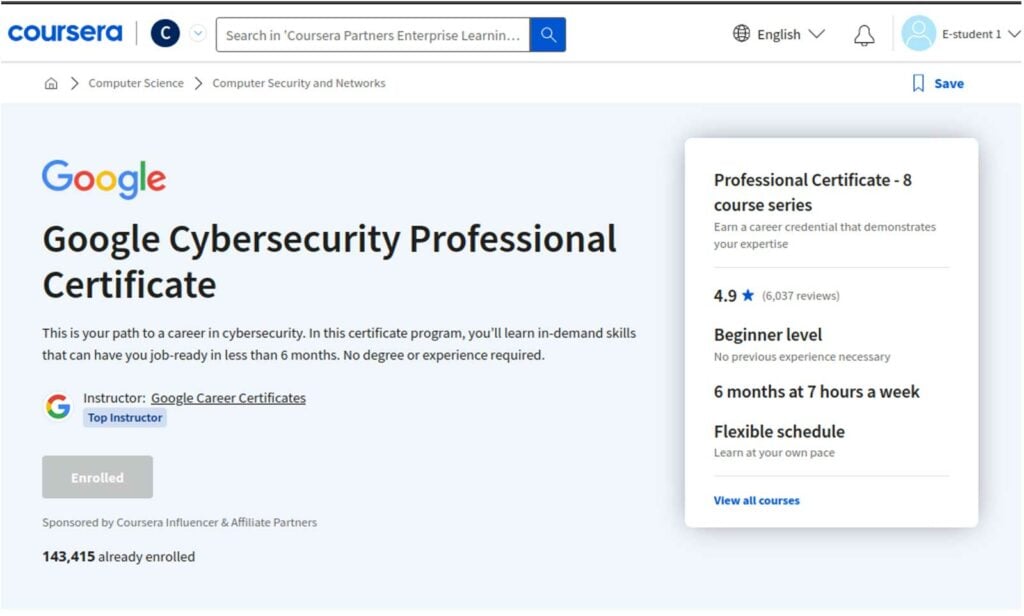
The Google Cybersecurity Professional Certificate serves as a starting point for professionals who want to pursue a career in cybersecurity and are looking for a flexible way to learn the necessary skills. Listed on Coursera as a beginner-level program, neither a university degree nor prior experience is required for those looking to enroll. The program features courses covering the common terms, frameworks, and tools to prepare a learner for an entry-level cybersecurity job, including identifying threats and risks, using playbooks to respond to threats and risks, securing networks against intrusion, and automating tasks with Python.
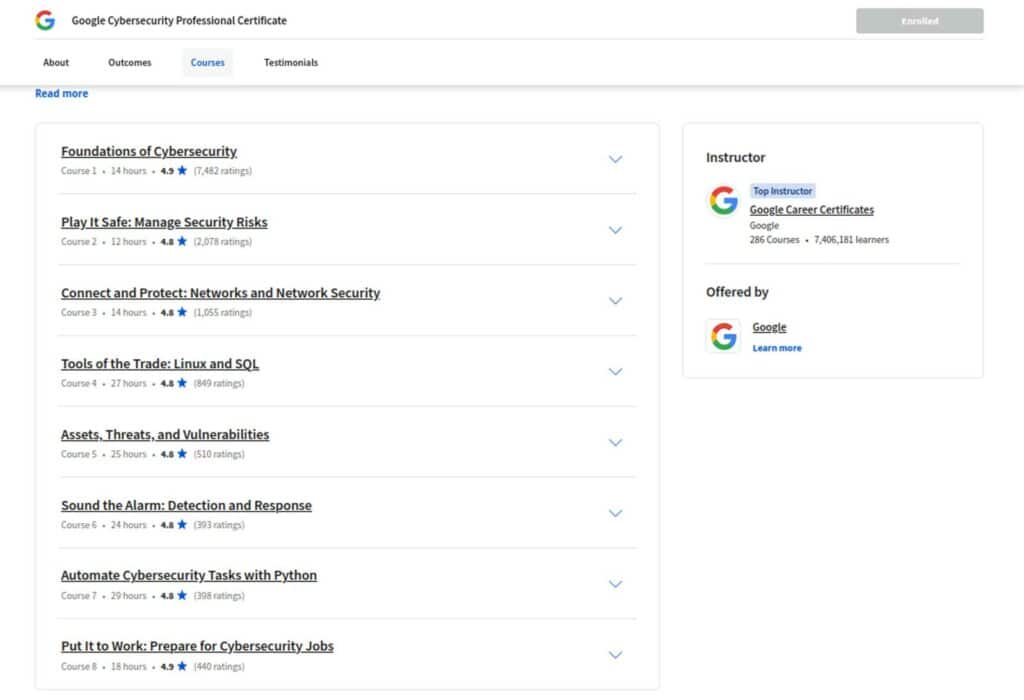
The course has a well-organized syllabus that divides the content into eight different courses, with each of the courses building upon the foundation laid by the previous course, helping ensure that you grasp complex cybersecurity topics in a logical sequence. Each course has four modules with several quizzes and activities to reinforce the concepts being covered.