
Review of Coursera’s Microsoft Azure Developer Associate (AZ-204) Professional Certificate
Dive into this review to uncover the ins and outs of becoming an Azure Developer —your gateway to mastering Azure cloud development!
Are you looking to get into the field of cybersecurity? In this review, we’ll have a look at whether this nanodegree from one of the leading online IT course providers might help you get there.
E-student.org is supported by our community of learners. When you visit links on our site, we may earn an affiliate commission.
4.7 / 5
The Introduction to Cybersecurity “nanodegree” from Udacity offers a comprehensive overview of the effectiveness of equipping people with vital cybersecurity skills. Covering essential topics like cybersecurity foundations, threat intelligence, incident response, and governance, the program provides a solid foundation for navigating the cybersecurity landscape. Practical projects and expert guidance enhance learning and give students a grounding in addressing real-world problems. The program is recommended for beginners to seasoned practitioners seeking to enter or advance in the cybersecurity field.
At a time when cyberattacks constantly threaten our digital assets – whether those of businesses, public services, or individuals – there is a greater need than ever for qualified professionals who can assess, manage, and monitor computer systems to keep them secure. Cybersecurity affects every part of our everyday lives and is not only a worry for governments and big businesses. Almost every facet of contemporary life depends on safe digital infrastructure, from individual bank transactions to the workings of global firms. And with the rise of cyber threats like ransomware, phishing, malware, and DDoS assaults, there is a severe lack of qualified individuals to keep everyone safe.
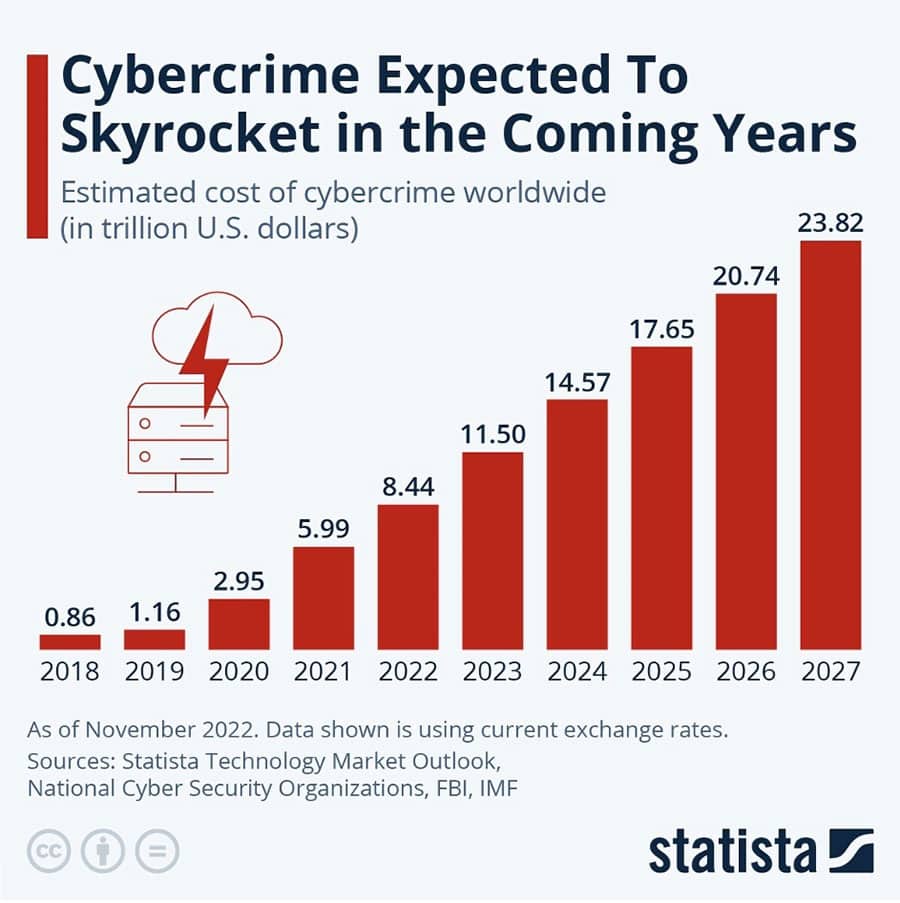
Given this situation, it’s critical to have high-quality introductory programs to induce new professionals into the field of cybersecurity – an area that I am particularly interested in as a graduate in computer science and information security. Coming from one of the leading providers of IT-related online courses, the Nanodegree program “Introduction to Cybersecurity” on Udacity comes across as a particularly interesting option, promising students the necessary information and real-world experience to understand cybersecurity.
In this review, we will examine every aspect of this program, including its relevance, real-world applications, and possible impact on future employability. Let’s get started!
The “Introduction to Cybersecurity” is a program offered on Udacity. As a “Nanodegree” program, it is one of the platform’s flagship offerings (in contrast with their more mundane “courses”), which go more in-depth on a topic and help prepare students with real-world case studies and projects. Unlike many other platforms, your assignments are looked at by paid reviewers, ensuring that those who complete the courses have actually learned something and who also provide feedback to make sure that you end up with portfolio-ready projects.
The program gives you a strong basis on which to develop your expertise in cybersecurity by exploring the fundamental ideas, important security measures, and industry best practices in the field. You will start out by exploring basic things like tutorial viruses but also get introduced to more advanced skills needed to evaluate risks, spot vulnerabilities, and put effective security measures in place through a combination of classroom instruction, practical exercises, and real-world applications. Every aspect of the program, including cybersecurity foundations, threat intelligence, incident response, system defense, governance, risk, and compliance, is crucial in molding the upcoming generation of cybersecurity experts.
This is a beginner-level program without any prerequisites apart from being able to operate a computer – and having basic knowledge about how to operate a command line interface. However, as it goes fairly in-depth, it’s also a suitable option for those with more extensive IT experience who are new to the area of cybersecurity.
Note that the focus is on Windows environments, which is suitable as it is the dominant operating system on the market. However, this makes the program less relevant for those working on other kinds of environments.
The indicated course length is three months – but as the pace is flexible, you can complete it in a shorter or longer time as you need (however, note that the cost of the program depends on the time taken to complete it, as access is only via subscription to the platform).
The program consists of four main courses, each expected to take 3-4 weeks to complete:
Each of the courses includes 6-7 lessons, each covering a major topic. These consist of video lectures, additional reading and resources, quizzes, and exercises. Each course also ends with a major graded project, where you are walked through creating a solution to a real-world problem.
The program also includes an introductory course to help you navigate your way through the program, as well as a final “career services” lesson to help you improve your LinkedIn profile.
To give you a better idea of what is covered in the program, let’s have a look at each of its courses in more detail.
The Cybersecurity Foundations module is the starting point, providing learning with a comprehensive understanding of essential concepts, principles, and practices in cybersecurity. Through this module, you will delve into the intricacies of cybersecurity fluency, gaining an understanding of terminology, concepts, and methodologies prevalent in the field. The course explores vulnerability management strategies, mastering techniques for identifying, assessing, and mitigating vulnerabilities across diverse computing environments.
Additionally, the module delves into identity and access management fundamentals, equipping you with the knowledge and skills to manage user identities, access privileges, and authentication mechanisms effectively. You’ll also learn about threat intelligence approaches, which help them to anticipate and proactively assess new cyber threats.
This module provides a strong foundation for learning fundamental cybersecurity principles, crucial security controls, and industry best practices.

The module on Threats, Vulnerabilities, and Incident Response delves into the ever-changing world of cyber threats, vulnerabilities, and the necessary tactics to reduce risks and handle security incidents successfully. This course goes into the anatomy of cyber threats, providing an understanding of the strategies, tactics, and motives used by threat actors to compromise digital assets. In addition, it will help you become proficient in locating, ranking, and fixing vulnerabilities in various computer settings.
The program will give you the tools to create cybersecurity incident response playbooks (which was particularly interesting, in my view) and get familiar with offensive security tactics, ethical hacking, penetration testing, and red team activities.
The Defending and Securing Systems curriculum gives you the technical know-how and hands-on experience you need to defend computer systems from online attacks. You explore the complexities of cryptography in this lesson, learning the encryption methods, cryptographic algorithms, and cryptographic protocols necessary to protect data while it’s in transit and at rest. In addition, you investigate security information and event management (SIEM) platforms, learning about threat detection techniques, event correlation, and log management.
The course also covers systems security principles, giving you the ability to successfully mitigate common security vulnerabilities, safeguard network services, and harden operating systems. In addition, you become proficient in network security best practices, firewall configurations, and intrusion detection/prevention systems (IDS/IPS), which help students create and deploy resilient defenses in a variety of computing environments, as you’ll practice in the project at the end of the course.

The module on Governance, Risk, and Compliance offers you a thorough synopsis of the cybersecurity domain’s governance, risk, and compliance environment. You’ll learn about the significance of cybersecurity governance frameworks throughout this subject, as well as the industry standards, legal regulations, and compliance frameworks that control cybersecurity operations. In addition, you study cybersecurity compliance requirements and become proficient in coordinating organizational procedures with legal requirements and industry standards.
The course also examines risk management techniques, giving you the tools you need to recognize, evaluate, and successfully reduce cybersecurity threats. You also learn how to create cybersecurity policies, manage stakeholders, and implement security risk remediation techniques, which helps companies construct a proactive risk management and compliance culture.
Most graduates of the Introduction to Cybersecurity Nanodegree are very positive about the program. In their reviews, they particularly emphasize how the program effectively provides you with the academic knowledge and practical skills necessary for success in the cybersecurity field. The program’s thorough treatment of cybersecurity foundations, practical applicability, and conformity to industry standards and best practices were highly praised. The graded projects were found by several reviewers to be at an appropriate level – neither too easy nor too difficult.
In terms of criticism, the main point of contention has been problems with the virtual machines that you need to use for the projects, which have been very slow and buggy for some users. This has, however, hopefully, been addressed in the latest updates to the course. The focus on Windows environments also surprised some of the reviewers, who nonetheless found the course useful.

Although Udacity’s Introduction to Cybersecurity Nanodegree program provides a strong foundation in cybersecurity, you can further improve your skill sets and career prospects by adding specialized courses or certifications to complement the program.
Having completed the Introduction to Cybersecurity Nanodegree program, I found that I had greatly expanded my knowledge of cybersecurity principles, techniques, and approaches, even with a relevant university degree in my pocket. The practical projects, real-world simulations, and hands-on exercises like SIEM frameworks allowed me to get used to these tools to identify threats, put security controls in place, and handle security crises. In addition, the well-organized course material and professional coaching made learning easy and helped me understand difficult ideas so I could use them competently and confidently in practical situations.
I recommend this program for anyone looking to start a career in cybersecurity or expand their skill set in this exciting industry. This curriculum will be especially helpful to aspiring cybersecurity professionals, security analysts, network administrators, and IT managers as it will equip them with the information, abilities, and real-world experience needed to succeed in the constantly changing field of digital security.


Dive into this review to uncover the ins and outs of becoming an Azure Developer —your gateway to mastering Azure cloud development!

Here are five Ivy League online courses that’ll give you a world-class education for only a fraction of the price of an Ivy League degree.

Learn how to use R, the “golden child” of data science, with the best R courses.